Traditional SDLC security tools analyze artifacts: code, pipelines, infrastructure, and runtime environments.
What they often miss is how risk entered the SDLC in the first place.
Developer actions such as:
researching solutions,
selecting dependencies,
choosing tools,
using AI assistants,
can all introduce security and compliance risk long before scanners are triggered.
Beyond Left reflects the need to observe and govern these actions, not just the resulting code.
Beyond Left does not replace shift-left security, CI/CD controls, or scanners.
Instead, it highlights a blind spot that Developer Security Posture Management fills.
By creating a historical record of development activity tied to developer identity and actions, Archipelo enables organizations to:
Understand how risk originates before code exists
Attribute downstream vulnerabilities to earlier decisions
Reduce repeated risk caused by ungoverned behaviors
Strengthen compliance evidence across the SDLC
This developer-aware visibility is what makes “Beyond Left” actionable.
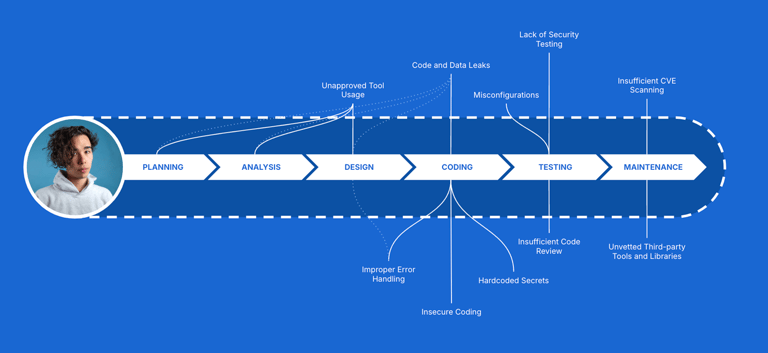
Without developer-level observability, organizations lack insight into early-stage risk, including:
Unapproved Tools and Shadow IT. Developers may install IDE plugins, browser extensions, or external services outside approved policies—expanding the attack surface without detection.
Insecure AI-Assisted Development. AI tools can introduce insecure patterns or reuse vulnerable code when used without governance or attribution.
Risky Research and Code Sourcing. Copying snippets from untrusted sources or relying on outdated guidance can introduce vulnerabilities long before scanners run.
Repeated Behavior Patterns. When risk is not attributed to actions and identity, organizations cannot identify recurring issues across teams or workflows.
Beyond Left highlights these risks—but DevSPM provides the mechanism to address them.
Security incidents consistently demonstrate that risk introduced during development often bypasses traditional controls:
Insider Threats and Identity Mismanagement, Uber Breach (2022):
Compromised developer credentials allowed a hacker to gain access to sensitive systems, demonstrating the importance of monitoring developer activity to prevent insider threats.
AI Code Vulnerabilities, GitHub Copilot Security Flaw (2024):
Researchers revealed that AI tools like GitHub Copilot occasionally suggest insecure code snippets if your existing codebase contains security issues, underscoring the need to monitor and govern AI-driven code development.
Archipelo enables Beyond Left outcomes through Developer Security Posture Management:
Developer Vulnerability Attribution
Trace scan results and vulnerabilities back to the developers and AI agents who introduced them.Automated Developer & CI/CD Tool Governance
Scan developer and CI/CD tools to verify tool inventory and mitigate shadow IT risks.AI Code Usage & Risk Monitor
Monitor AI code tool usage to ensure secure and responsible software development.Developer Security Posture
Generate insights into security risks introduced by developer actions across teams.
These capabilities provide visibility into how risk enters the SDLC—not just where it surfaces.
Beyond Left is best understood as a transition point in security thinking:
From scanning artifacts → to understanding who acted, how risk entered, and why it keeps recurring.
Developer Security Posture Management makes this possible by making developers—human and AI—observable across the SDLC.
Archipelo strengthens existing ASPM and CNAPP stacks with developer-level observability and telemetry—allowing organizations to address software risk at its true origin.
Contact us to learn how Archipelo strengthens your existing ASPM and CNAPP stack with Developer Security Posture Management.